Complete solution to setup AWS Directory Service and domain join with EC2 in a private Subnet and connect to AD using AWS System manager. Welcome to Bastionless AWS Cloud.
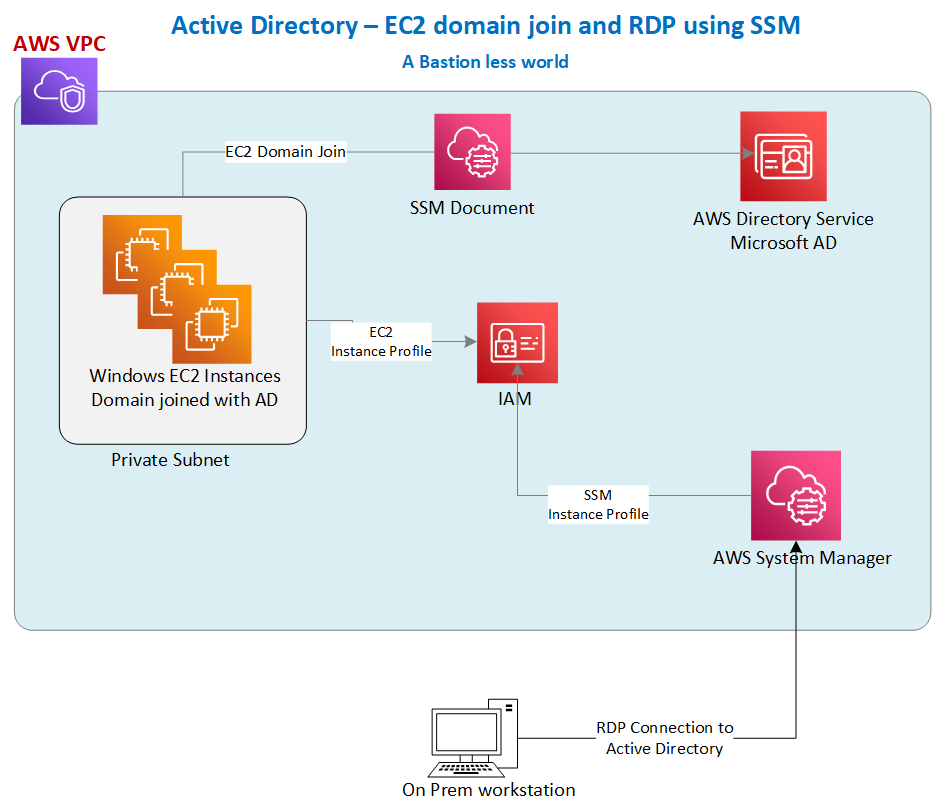
Use case :
Set up AWS Directory Service in AWS cloud ( Standard edition) in a Private Subnet , launch a Windows instance in a private subnet and domain join the instance with AD, and RDP into Active Directory server from a local desktop ( outside VPC) and manage the directory ( add groups , users etc).
Refer to Git repository for the complete terraform code and clone it – https://github.com/nyalavarthi/aws-active-directory
Implementation details:
Note : make sure your System manager is already set up , refer to these prerequisites and complete the setup before running the terraform scripts.
Terraform workspaces are used for this project, take a look at my article on workspaces with an example to get some familiarity, it will help you effectively manage different environments & aws accounts with a single code base [variable files to be specific] .
Clone the terraform repo and make changes to variables.tf file as per your environment and account. copy AWS Access key and Access Secret Key into command prompt
set AWS_ACCESS_KEY_ID=****
set AWS_SECRET_ACCESS_KEY=*****
Follow the commands from Readme file from the repo to create new terraform workspace and initialize the terraform code.
After successfully applying the changes you will have following resources created in the AWS account
- aws_directory_service_directory
- aws_ssm_document
- random_string
- aws_ssm_parameter
- Windows EC2 instance
- IAM instance profile Role
- aws_ssm_association
Here is brief explanation of each AWS resource that was created as result of the terraform project and the purpose of each service.
- aws_directory_service_directory : AWS Managed Microsoft Active Directory created in two private subnets for high availability
- aws_ssm_document: System manager document used by SSM for domain joining EC2 with directory service.
- random_string: random string to be used as admin password for directory
- aws_ssm_parameter: SSM parameter store to save the encrypted password for AD admin user.
- aws_instance : Windows EC2 instance domain joined with DS
- aws_iam_role : IAM Instance profile roles for both EC2 and for SSM
- aws_ssm_association: Associate the SSM document with EC2 instance.
How to use SSM to RDP into AWS Directory Service with out Bastion Host ?
Open command prompt and enter AWS credentials ( Access Key & Secret Key)
TO check if EC2 is successfully domain joined, use the following SSM commands in sequenceaws ssm start-session --target yourInstanceId
Get-WmiObject Win32_ComputerSystem
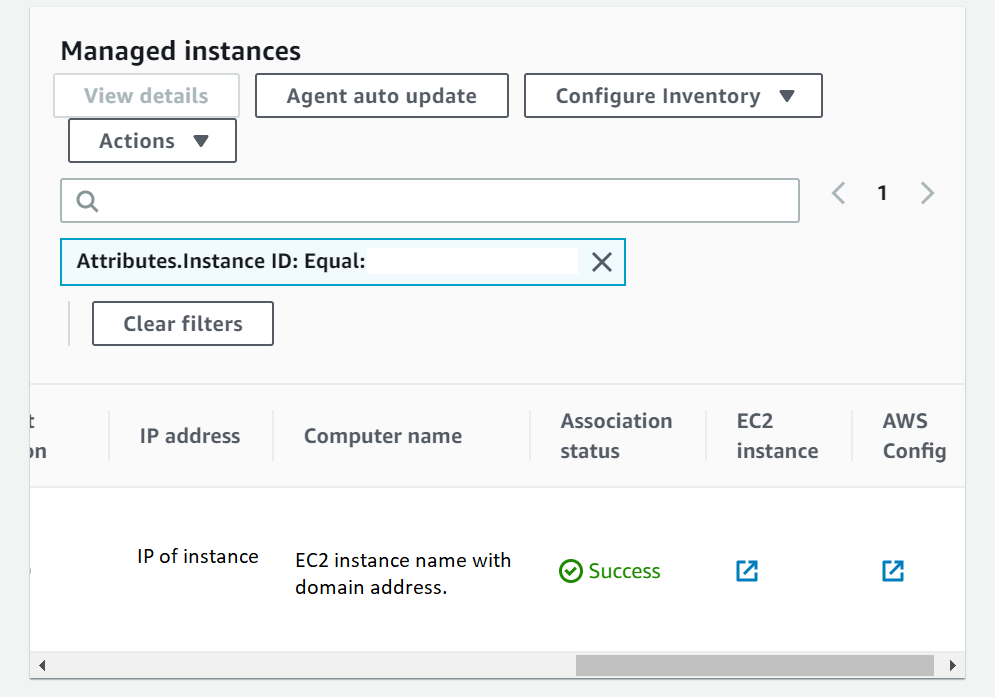
Alternatively you can also go to AWS System Manager console -> Managed Instances -> search by Instance ID and from the results see if the domain join is successfully – as shown in the below screenshot.
Once you verified your instance is domain joined , use below SSM command to initiate connection with Session Manager , port number 3389 is the port you will use to RDP. and Port 55678 is what you would use to connect o session manager via RDPaws ssm start-session --target yourinstanceid --document-name AWS-StartPortForwardingSession --parameters "localPortNumber=55678,portNumber=3389"
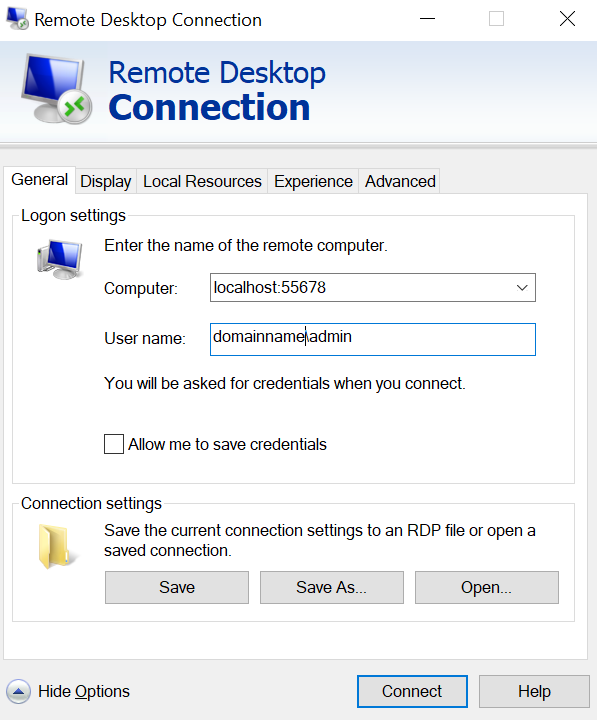
RDP Connection to EC2 :
Start Remote desktop Connection and enter localhost:55678 (same port you provided in the SSM start command) in the computer name
enter your domain name ( refer to the dns_short_name variable from terraform code) \admin as User name
Find the random password that is generated from Parameter store , search by this string unless you modified the terraform code – /directory/password/master
Once DRP connection is successful, follow the instructions from this Amazon video to setup the admin tool on the EC2 instance so that you can start managing AWS Directory service ( ex: adding groups , users, Etc).
Please note that the steps mentioned in this video to create EC2 are different and they are meant to create EC2 in a public subnet and it doesn’t require SSM.
You can also refer to this aws documentation for installing the AD tools on your EC2 Instance
Assign the aws managed group “AWS Delegated Server Administrators” to your users / groups to allow users to manage the EC2 instances that are domain joined.
When you create users, groups in the directory and want to find what roles you can assign to the groups , refer to this aws documentation
Lee me know if you have any questions or issues setting up the terraform stack .